
dajacob33
-
Posts
8 -
Joined
-
Last visited
Content Type
Events
Forums
Downloads
Quizzes
Gallery
Blogs
Posts posted by dajacob33
-
-
18 minutes ago, Orton Rd said:
This is the original fortune cookie by AKB48 the Thai version is a total copy, like an Elvis or Beatles cover band, no originality at all. Smacks of desperation by the PM to me.
That's because they're the OFFICIALLY LICENSED 48's SISTER GROUP. They're licensed directly by AKB48 and are allowed to use the 48 name, songs, etc. Even Izurina (Former AKB48 member) is transferred to BNK48.
If you look at it that way, it's a copy. But they're officially licensed. And why do they have to use only original songs if they license 48's name in the first place? In that case, they don't need to be "BNK48" at all.
So you're saying that it doesn't matter that they're officially licensed or part of the 48 sister group and that they're considered cover group that's blatantly copying someone else?
Do you consider these "cover groups" blatantly copying too? (Well, except for SNH48. I don't consider them official anymore as they broke the agreement with AKB years ago and no longer official sister group)
Any I guess you consider NMB48 singing 365 days of paperplanes a blatant copy too?
I don't really know what to say. 48 is a franchise. It's not a single band or single group. So referring to sister group as a cover group doesn't sound right. That's very disrespectful to the groups.
-
1 hour ago, Orton Rd said:
I would have thought it not very Thai to want the support of a cover group who blatantly copy a Japanese one?
He would get more votes with the real onesWell, BNK48 is very popular among Thai teenagers and young adults and often gets promoted in other products, so if the goal is to attract these target audiences to check the campaign out then BNK48 is not a bad choice at all. It works better than just having ordinary Thai singers, actors, actresses in there. The BNK48's fanbase is also very active.
And I'm not really sure why you're saying that BNK48 is a cover group blatantly copying AKB48 and fake. That implies that they're not an official 48's sister group and just stole 48's name for themselves? Or maybe I didn't get the sarcasm.
The group is as official as other foreign sister groups such as JKT48, MNL48, MUM48 and SGO48.
So they are allowed to use the same model as AKB48, same songs (And translated), etc because they're literally the AKB48's sister group. If that means blatantly copying AKB48 then I don't know what to say. It's like saying 48 groups mentioned above + other sister groups in Japan are blatantly copying AKB48. Might as well say that any AKB48 2nd Gen members and later Gens are blatantly copying the 1st Gen in that case.
Also about the votes he would get with the AKB ones. I think it's actually the opposite. Actually not that many people in Thailand follow AKB and their other sister groups actively. Many just follow and care about BNK48. Many BNK48 members didn't know much about AKB48 before coming for an audition too. And I think I remember in Japan Expo where they had AKB48 go on stage before BNK48, some fans were being disrespectful and shouting "Where's BNK48? I want to see BNK48!" too.
-
On 6/17/2018 at 9:52 AM, muratremix said:
Perhaps this is a malware intended to monitor facebook posts for users in Thailand?
Like, government issued?
China insists installing similar malware in north-western china (uighur area).
3bb does dns hi-jacking so using 8.8.8.8 or 1.1.1.1 redirected to 3bb dns servers.
It would be possible to infect android phones with bogus dns and servers if they wanted.
Is there a way to verify for sure that the DNS is being hijacked? I tested with DNSLeak sites and whoismydns.com and the results showed I'm using the correct DNS.
This method (https://community.cloudflare.com/t/verifying-router-is-using-1-1-1-1/15004/6) also returned the correct DNS server.
Unfortunately, with 8.8.8.8, 1.1.1.1 or OpenDNS servers I still get the malware codes, so something weird is definitely going on with 3BB.
On 6/18/2018 at 2:45 PM, mwbrown said:OK, I successfully flashed DD-WRT into my Asus router. I feel better about not having the lousy Asus firmware but there's still the larger picture.
I tried the bad URL again and after dozens of refreshes on Chrome, I never get the bad code.
I decided to try the same URL in Opera and believe it or not, on the first try Windows Defender catches it as Trojan:HTML/Brocoiner!rfn
So, something weird still going on.
Did you make any headway with 3BB? Ask for tech support and whisper "Shibboleet..."
Hmm... So the malware is still there regardless of whatever firmware is being used. Probably something is wrong within their networks.
Also I haven't contacted 3BB yet as I don't have the time. I will find the time to explain this to them later.
Meanwhile, you guys can contact them too. So it isn't just me reporting and they will be more likely to look into this issue.
Thanks, everyone!-
 1
1
-
-
1 hour ago, catman20 said:
?
I thought the tl;dr was not that bad... compared to OP lol ?
Any shorter will be like telling other 3BB users to visit some "random" URL and ask if they're infected by malware or not. At least I had to tell where did I get that URL from.
Anyway, is anyone here able to find the real IP or URL of that malware-infected page? Maybe we will know more about it.
-
10 hours ago, miamiman123 said:
You are such a genius...I know u will figure it out
I'm not trying to be a smart-ass ? I'm just very frustrated because I've done like 15 factory resets on both ONT and router, lots of computer/phone virus scans and the problem is still there... And on top of that, there were no reports of people having similar issue so I don't know what's really happening to my router.
10 hours ago, catman20 said:Thanks for the reply! I realized I wrote the OP too long and many people probably ignored it.
YES !
I was going to add tl;dr to the first post but somehow the forum didn't show Edit button anymore. I will add here.
tl;dr -
My ISP is 3BB. I'm on Fiber. I noticed something weird going on with my Android 5 phone. There's a popup "Sign-in to WiFi network" showing up when I first connect to 3BB WiFi for about 4 days now.
After I clicked it, the popup that reads "Please update to the latest Facebook version" appeared. I searched on the internet. Figured out it's the sign of "Roaming Mantis" router malware infection. (If you want to know more about this malware, please check the URLs in first post)
How did I know the malware was embedded in that generate_204 page? The pop-up title was "connectivitycheck.android.com says -" so I googled this URL and founds lots of articles mentioning this is the URL that the phone pings to check for the internet. Different Android versions and even phone from different manufacturers may even have their own custom generate_204 URLs, so unless your phone pings http://connectivitycheck.android.com/generate_204 then you won't get the malware popup on initial WiFi connection. (Many Android 5 and some 6 phones use this URL though)
So if you're on 3BB. You can visit http://connectivitycheck.android.com/generate_204 on Chrome. Please refresh it as many times as you can because it won't load the infected page 100% of the times. I think it's anywhere from 30-70%. So if you're infected you will eventually get the malware pop-up.
You can visit the URL on your PC too. But you will need to right-click and "View page source" or "Inspect" and see by yourself if there are any malware codes in there as the pop-up will not automatically show, unlike on phone.
9 hours ago, gabruce said:I have 3BB Fibre (Chiang Mai) and the page comes up clean for me.
Thanks for reporting. Did you refresh multiple times? To be sure you can clear DNS cache and do full-refresh too. (CTRL+F5 or CTRL+R)
Sometimes I don't see the malware codes too. It won't show 100% of the times.
9 hours ago, mwbrown said:I've noticed your symptom on my Android phone a couple of times in the last few days too. It's a Huawei GR5 2017 and I've received two security updates in the last month, the latest Android security patch level marked 1 May 2018 for it so I suspect it's as good as I can get.
I have a 3BB DSL modem, Huawei model HG630 V2 with a complex password that I set two years ago, connected to an Asus router. Similar to your setup.
I get the hacked code when I view source for generate_204!!!
I'm going to reset the modem and change the passwords, and flash the Asus, which I know is out of date because it's a piece of shit and breaks functionality with every new firmware version. I have it on my to-do list to change to DD-WRT or Tomato so I think I'll just do that now.
Thanks for the report! Now I know there's at least one another person with the same issue like me. According to your report; Now I know that 3BB DSL user with different Huawei modem can be infected too.
Please report back again after you've done resetting and upgrading your Asus router! I'm looking forward to seeing the results.
In case you still see the malware; I suspect Huawei modems, ONTs are probably being mass targeted and exploited. Or maybe this is an issue with 3BB internal networks.. Because according to analysis articles, they say the normal sign of infection includes having your router's DNS settings literally changed to rogue servers. But I have never seen it changed to anything else.
9 hours ago, RBOP said:Your phone sounds infected. Take it to authorized Samsung dealer for checking and reset. Also if you call 3BB they can check your router by remote and if you insist enough they will replace your router.
Thanks for the advice!
For the phone: I already scanned it multiple times and I'm pretty sure my phone is clean. I only see malware codes when I'm connected to 3BB internet. On 4G network it's totally clean. On top of that, I see the same malware codes in this URL on my PC too. But when I tether 4G connection to my PC, I don't see it anymore. So it must be the Huawei router or 3BB network.
I will probably contact 3BB and explain this to them.
8 hours ago, asiamaster said:Exactly the same happened to me two days ago at the 4 Kings sauna in Pattaya. Never had that problem there before and back home no problem either. So yes probably in their router.
Thanks for the report! Another person with the exact same issue! This will probably make it easier for me to explain to them because now I know there are other people getting it too. After narrowing down the possible issues.
Are you on Fiber or DSL? Is your modem, router, ONT Huawei?
8 hours ago, rberlint said:A red flag for me is that the 204 site is "http://connectivitycheck.android.com/generate_204 " instead of " https://connectivitycheck.android.com/generate_204".
I don't think the non-HTTP of this URL is the red flag because after googling, I see all sites refer to this URL as a non-HTTP. So it's probably Google themselves that set it up this way.
7 hours ago, masterpasser said:Try an alternative DNS provider like CloudFlare it provides additional safety apparently
Settings 1.1.1.1 and alternative 1.0.0.1
I tried this DNS and still see the malware. Same with OpenDNS and Google DNS.
I never use 3BB DNS though. I've always used Google DNS in the past.
It's weird.. I thought it might be related to DNS poisoning but no matter what DNS I use, I still see the malware.
4 hours ago, KBTexas said:Interestingly, it makes no difference as https:// gets an insecure connection. I tried going there and the page is blank. The following are screen captures of the connection data and the page source.
There is much more to this, but you get the idea.
My router is from 3BB and is an HG8145V. However, I do not experience any issues with the computer or the phone, so I am not sure if this is something that is really an issue. Sophos reports the MacBook Pro clean (though it did catch the Coinhive issue a few weeks ago) and Sophos Mobile Security reports the phone clean. Where did you get the URL http://connectivitycheck.android.com/generate_204 in the first place? It was a new URL on both my phone and computer with no existing cookies, etc.
If you figure out what is going on, please report back and let us know.
Regards,
KB
1Thanks for the report!
Same! If I load that URL with https then it's clean (But it's also totally blank) The malware will only show on http.
And yes, the code you've shown is the same code that I'm seeing right now.
On the computer, you won't see any issues because the PC has no use of this URL at all. You will have to visit it manually to even know that the malware is there. I'm just providing the direct URL so that you guys can check on your preferred devices ?
On your phone, I think the reason that you don't have issue is because it's pinging to other generate_204 URLs. As I mentioned earlier; different Android versions ping different URLs. Right now I know that most Android 5 and some Android 6 devices ping this specific URL. And even if your Android is 5 or 6, your phone manufacturer may host and make use of their own custom URL.
I have Android 5, 7, 8 phones and I only have this issue with 5 because it pings this URL on WiFi connection start. Thus triggering the "Sign-in to WiFi" and malware pop-ups.
As to how I got this URL in the first place; I noticed that the malware pop-up had the title "connectivitycheck.android.com says -". At first, I didn't know about this URL but after googling for a while, I figured out that it's total legit URL used by Android phones for pinging. The URL is owned by Google.
-
On 6/12/2018 at 9:19 PM, muratremix said:
if HG8245H in bridge mode there is no way it can be infected.
suspect your tp-link router.
maybe upgrade firmware, reset to factory defaults after upgrade etc?
Thanks for the reply! I realized I wrote the OP too long and many people probably ignored it. I will edit OP post to include tl;dr some time later. However, this reply will probably be as long as the OP.
------------------
As for my TP-Link router, I already upgraded it to the latest firmware (It's actually not so new, the latest firmware was released at the start of year 2018)
At first I thought my TP-Link router was infected too. So I factory reset it, immediately changed admin and WiFi passwords (Every time I use randomized unique passwords, with symbols), made sure Remote Management is disabled and changed to more reliable DNS (Like Google DNS)
I did this multiple times. Every time I test by visiting the page http://connectivitycheck.android.com/generate_204 both from my PC and phone and still getting malware codes in there (I load the page very quickly multiple times, and 70% of the time it will load the malware codes embedded in the HTML)
Then I got frustrated and wanted to verify that only the TP-Link is infected and not the ONT itself. So I disconnected the TP-Link router from the ONT and then factory reset the ONT. This time I just leave the ONT on Router mode and connect my devices directly to it then immediately applied the same security practices before connecting to the internet (Changed passwords, disable remote access, etc.)
And guess what. Still seeing malware codes on http://connectivitycheck.android.com/generate_204
---------
So my current situation is -
1) My PC & mobile devices: I can verify that all my PC and mobile devices are clean. I keep them all up-to-date, installed antivirus and don't download shady stuff. Most importantly, I tried visiting generate_204 page using my phone's 4G network and the malware codes never showed up on that network.
2) My TP-Link router: It shows no signs of infection in the log and in the router config itself, including DNS settings. From Kaspersky and Securelist blogs they say the malware literally changes the router's DNS settings if you're infected. I can verify that my router config is unchanged. I also double-checked by factory resetting it multiple times. Every time I will still see malware on generate_204 page. So I'm not really sure if the malware is capable of constantly targeting and attacking my router the moment it connected to the internet? How?
3) My ONT from 3BB: In the past, the ONT has always been set to Bridge mode, for over a year. As per your advice it shouldn't be infected. So I tested by doing factory reset on the ONT and then use it in Router mode. And.. I still see that damn malware in generate_204 page ? I don't know why... Is the malware somehow instantly targeting my 3BB ONT too?
It's very weird. But it's worth mentioning that the signs of infection that I'm seeing is a bit different than what Kaspersky mentioned in the articles.
Key points from Kaspersky articles -
1) Popular sites like Google, etc. should show malware codes.
2) With this malware, if you use iOS device. It will redirect you to fake security.apple.com site (Phishing site) | Please note that this fake security.apple.com is impossible to reach if your router isn't infected. Because there's no real security.apple.com anywhere, and it will require rogue DNS server to redirect you to the actual phishing site.
3) Router's DNS settings should literally be changed to rogue's servers and should be visible from inside the router config page.
Signs of infection that I'm seeing -
1) Right now I can only see malware codes only on generate_204 page. I checked other major local and international bank sites, Google, Apple, Yahoo, etc. and none of them are infected.
2) I tried loading security.apple.com multiple times (For about 10 minutes) and I never get redirected to any phishing site. It never loaded anything.
3) My router logs don't show anything suspicious and configs are unchanged.
So right now, my suspicion is on the 3BB itself. I'm not sure if they messed up something and is currently serving the infected page to users? Or maybe their ISP-level router or their network thing is somehow infected?
Or maybe HG8245H devices are being mass-exploited?
So I would like to ask for your help if you're on 3BB (Especially if you're on Fiber plan with HG8245H ONT. But other devices can try too) Please visit http://connectivitycheck.android.com/generate_204 (Load it multiple times very quickly. Do this for few minutes. If possible try on both PC and mobile phone)
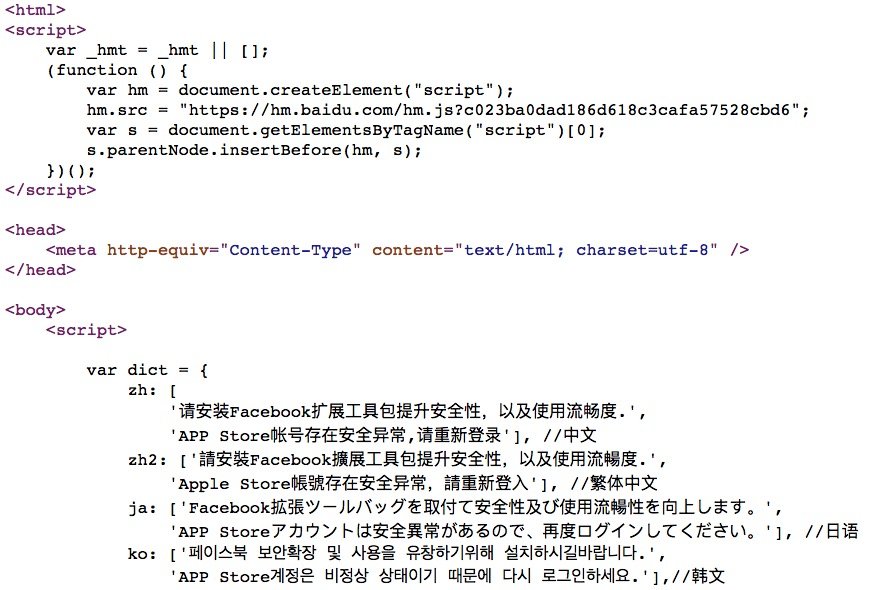
If you're infected, on PC it will load a blank page with hidden malware codes embedded in it. This can be seen by right-clicking and selecting "View page source". In there you will see tons of fake error messages in multiple languages, linked Baidu and CoinHive scripts, etc.
On mobile phone it will be easier to notice as it will show the pop-up dialogue. If your phone locale is EN. It will show "To better experience the browsing, update to the latest Facebook version." If in TH it will show "Please install Facebook extension to improve security blablablablabla, etc. etc." in Thai language.
I would like to verify if there are any other 3BB users having same issue like me, so I can narrow down the problem and see if it's just me that's infected, or is the problem on HG8245H or 3BB network.
*EDIT: Reconnected internet on my ONT and now it's not showing malware on that page for almost half an hour now. EDIT 2: I reconnected again and now got the malware immediately.. What?
-
Hello! I need help and advice with this malware.
My current setup is -
Huawei HG8245H ONT router from 3BB, set in Bridge mode ----> Connected to my own TP-Link router
I have disabled HG8245H's WiFi, disabled Device Access Control from WAN side, changed admin's password to something randomized & unique, deleted the default TR069 Route WAN connection settings and replaced it with non-TR069 Bridge WAN settings. Unfortunately, 3BB doesn't provide firmware updates for this device.
On my TP-Link router, I have latest firmware updated, Remote Management disabled, password randomized & unique and is using Google DNS servers (8.8.8.8, 8.8.4.4)
-------------
Since 9th June I've noticed something strange with my phone device. It's the Samsung J2 phone (Android 5 Lollipop)
So when this phone is connected to the router's WiFi. It showed the "Sign-in to this WiFi network" notification pop-up (Which never showed up before)
When I clicked on it. It loaded a page and showed a pop-up saying something like this in Thai "Please install Facebook extension to improve security, blabla" with the title "connectivitycheck.android.com says -"
If your phone locale is set to EN it will show pop-up in English saying "To better experience the browsing, update to the latest Facebook version." after clicking OK or Back button. It will show 404 error page in Chinese and then redirect to sohu.com (Chinese legit Internet provider site)
I thought it was strange so I searched around and found that this is the exact same behavior that will happen when the router is infected with "Roaming Mantis" malware. They say it's widespread in Asian countries and recently the malware got upgraded to support more than 20 languages and is now spreading to other Western countries.
Articles about the malware -
https://www.kaspersky.com/blog/roaming-mantis-malware/22427/
https://securelist.com/roaming-mantis-dabbles-in-mining-and-phishing-multilingually/85607/ (Includes some code analysis)
-------------
From the article: It seems the malware spreads by infecting poorly secured routers and simply changing DNS settings in it to their rogue DNS servers and when user visits most popular sites, it will redirect to their rogue servers and fool users into downloading Trojanized Chrome/Facebook .apk files. (In my case it didn't download any files and redirected me to sohu.com's 404 site. From what I read, this malware uses sohu's profile page as a Command & Control server to distribute the fake apk. So I got 404 error it was probably because sohu staff deleted those profiles already)
However, I checked the DNS settings in my TP-Link router and it wasn't changed from Google DNS that I've previously set. I checked router access log and nothing suspicious there. I also tested with DNSLeak site and the site reported that I'm fully using Google's DNS. I did the factory reset, immediately changed password, made sure Remote Management is disabled, firmware is up-to-date, changed to Google's DNS but the malware pop-up is still there.
I'm pretty sure my phone is secure and not infected. I don't install unknown apps, it's up-to-date and antivirus scan returned clean results.
To test that it's not my phone that's infected - I try visiting http://connectivitycheck.android.com/generate_204 page from my clean & protected PCs and after some full refresh (CTRL+R, CTRL+F5 for Chrome), I actually saw the same malware code embedded in this page's source code. And also when I disable WiFi on my phone and used my mobile network, the generate_204 page is clean.
This generate_204 page is made by Google and Android 5 pings this specific page on initial WiFi connection to determine if it has internet connection or not. Normally it should return HTTP 204 response and the page source code should be empty (Other versions of Android will ping different sets of pages, this is the reason why the malware pop-up won't show if you connect with other Android version phones, but if you want to check if you're infected. You can test it on any versions of Android phone by visiting the above generate_204 URL on your Chrome. The pop-up should show.)
Reference about the generate_204 page: http://www.ateijelo.com/blog/2016/09/11/make-android-believe-it-has-internet-access
So in my case, this page is infected with the malware and it has the Roaming Mantis code embedded in it. It also has the CoinHive cryptomining code in it too. This is why my phone started acting strange on initial WiFi connection and I saw the pop-up when I clicked on it.
So I'm trying to find out if my TP-Link router is really infected or not. I did factory reset multiple times and secured it. Tried different DNS servers like Google DNS, 3BB's own DNS, OpenDNS DNS, Cloudflare 1.1.1.1 DNS but the generate_204 page is still infected no matter what DNS server I use.
So I did the factory reset on 3BB's HG8245H, disabled WiFi, remote access, changed admin's password and tried again. And the page is still infected.
I eventually disconnected the TP-Link and did the factory reset on HG8245H again. This time I didn't switch it to Bridge mode and used it as the router itself (To find the starting point of infection. Making sure if the 3BB router itself is infected or not) I disabled WAN remote access immediately, changed admin's password to another unique one. Then I try visiting the generate_204 page with my clean PC. After full refreshing page few times, the infected code showed up again.
So I concluded that the HG8245H itself may be infected. But I checked the access log and didn't see any suspicious logins and DNS settings didn't get changed at all (According to articles, the DNS settings should've been changed if infected)
And the weird thing is that, according to the articles: other popular pages should redirect you to malicious pop-up thing too. But I tried those pages and they were all clean. This page: http://connectivitycheck.android.com/generate_204 is the only page I found that's infected with the malware code.
So here's the question: Is my HG8245H itself really infected? After all the resets and changing of security settings. It's still loading the infected version of the page. And it's only the generate_204 page that's showing the sign of infection, as opposed to the articles saying that other popular pages should be infected too.
Also during my tests, the DNS servers didn't get changed to any other unknown servers at all.
OR is it possible that 3BB themselves cached the infected version of the page and then serving it to users who visit this page?
-----------
For anyone on 3BB Fiber. Especially if you have the HG8245H. If you're interested to help me confirm this, you can try loading this page on PC and phone: http://connectivitycheck.android.com/generate_204 and view the page source code to see if it's infected or not (Do full refresh few times, preferrably try cleaning web browser cache, DNS cache before doing too. Sometimes I get the clean page, sometimes I get empty response error and the other times I get the infected version of it)
If the page is clean then the source code should be totally empty or showing like this -
<html> <head></head> <body></body> </html>
If it's infected, you will see script code linked to CoinHive in the <body> section and other scripts containing fake pop-up error messages and other stuff there.
-
 1
1
-


Celebrities joining Gen Prayut to launch new public campaign
in Thailand News
Posted
It won't be a problem as long as they are popular among Thai people, especially teenagers. They just need them to start watching TV programs about their campaigns (Even for 1 episode is good enough, I guess)
In fact, having Cherprang on board is a plus. Because she's not only seen as an entertainer but also as an Education Role Model. Having received awards such as role model awards, Buddhist Ambassador awards, studies Chemistry Science, had her version of Blue Bottle Experiment published in London's The Royal Society, etc.
So having someone who's in an idol group with huge Thai fanbase and is also great at academics? At least they made a good choice.
-----
And as you guys can see that 48 is a franchise. The same applies to McDonalds, KFC, Burger King, Pizza Hut, Dunkin Donuts, Krispy Kreme, X Factor, Got Talent, Who Wants to Be a Millionaire, etc. All of which are licensed in many countries around the world. So it's just not right to go around and say "UK KFC is a blatant copy of US KFC! No originality at all!" right? Or when you see Thailand's Got Talent and think "Wow, this show is a blatant copy of Britain's Got Talent! Shameful!". Well, that's the whole point of licensing a franchise. It should be in the same format or similar to the original. Can't stray too far.